Project LEAP: Central Banks Test a Quantum-Safe Payments Backbone
In order to quantum-proof the financial system and counter any threats to break the cryptographic encryption schemes used to ensure secure financial transactions and data, the BIS Innovation Hub launched Project Leap with several partners, including the Eurosystem Centre, Bank of France, Deutsche Bundesbank, Banca d’Italia, Swift and others.
Credit: Bank for International Settlements (BIS)
Why BIS pilots matter for systemic risk—and what they teach about migration costs
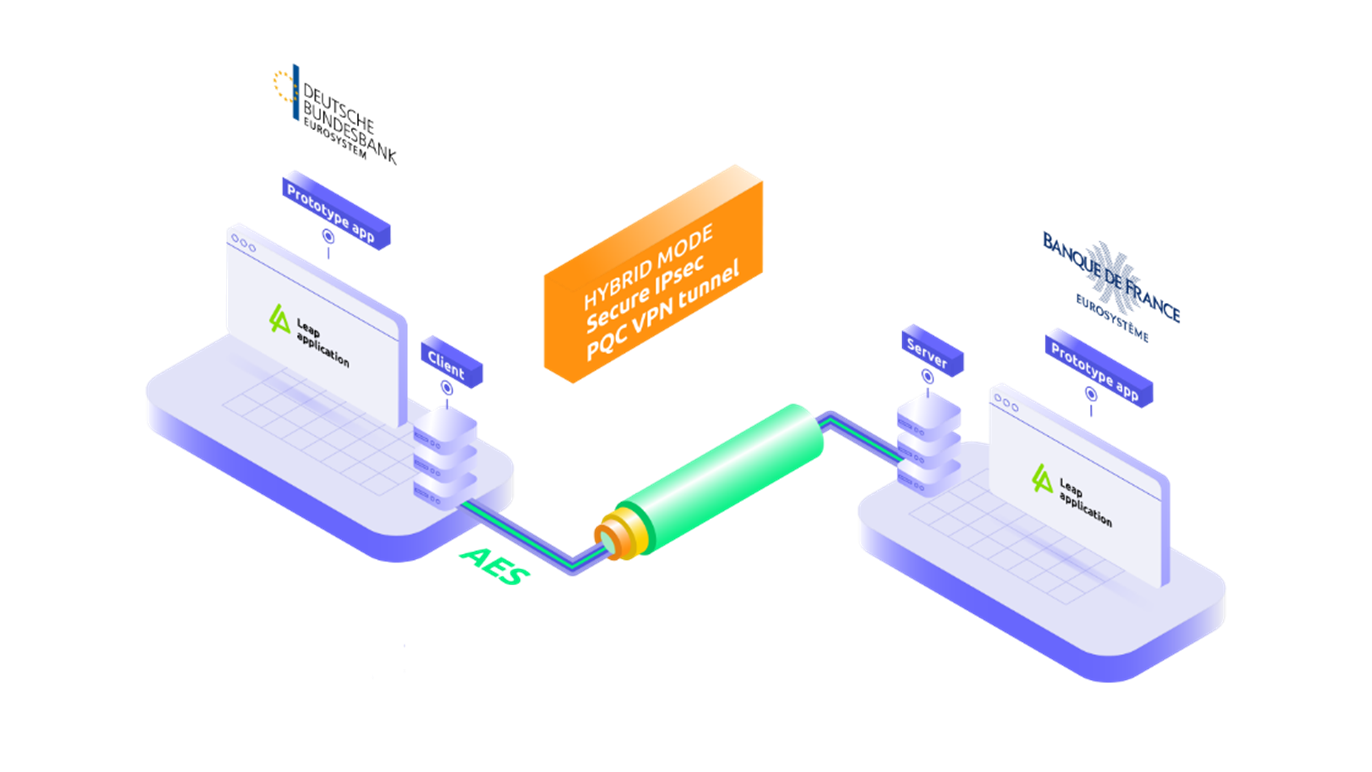
If you want to know how quantum impacts systemic stability, watch what central banks do, not what they say. The BIS Innovation Hub’s Project Leap is a multi-phase effort with the Eurosystem Centre and partners (Banque de France, Deutsche Bundesbank, Banca d’Italia, Swift and others) to prototype quantum-safe communications for payments infrastructures. Phase one demonstrated a hybrid post-quantum VPN carrying payment messages between France and Germany; the current phase is scaling the concept.
Why this matters: core payment rails—RTGS, ACH equivalents, cross-border messaging—run on layers of PKI and TLS that assume RSA/ECC hardness. If those fall, you don’t just lose confidentiality; you risk integrity and availability under sophisticated attackers. Project Leap is the least-regret move: test ML-KEM-based hybrids in live-like conditions, measure overheads, tune key lifetimes, and document the operational playbooks that national infrastructures will need.
BIS’s published materials are refreshingly concrete: Leap focuses on crypto-agile IT environments, not just algorithms in isolation, and treats migration as an engineering problem with inventories, gateways, and brownfield constraints. For commercial banks and critical vendors, that’s a cue to start mirroring the method—stage hybrids on internal links, then external, and validate performance and failure modes in advance of regulatory nudges.
LEAP also reframes cost. Many see PQC as a cybersecurity spend; BIS presents it as a practical financial-stability insurance. The risk isn’t just future decryption of archived traffic; it’s operational paralysis if a cryptographic break forces emergency patches across heterogeneous systems. Early pilots reduce that fragility by building institutional muscle memory—who changes what, when, and how you roll back without bricking endpoints.
For vendors serving central banks and market infrastructures, the go-to-market tone is standards-first and audit-ready. Align to FIPS 203/204/205, implement IETF hybrid TLS profiles, and bring measurable artefacts: handshake timings, CPU overhead on HSM-fronted services, error distributions under packet loss. Offer dual-stack support windows that match maintenance cycles for national systems (often years, not quarters).
The “secure versus fragile” question shifts with timing. Early movers get optionality—they can adjust algorithms as standards evolve, supported by crypto-agility and interop testing. Late movers face compressed change under pressure, the true recipe for fragility. BIS’s message is unambiguous: treat quantum readiness as part of resilience engineering, not an infosec niche.
Expect supervisors to reference LEAP as policy scaffolding—proof that PQC in payments has been exercised. Bringing your LEAP-aligned test results to the table will shorten approvals and make budgets easier to defend.